RPKI Explained – Resource Public Key Infrastructure
RPKI adds cryptographic trust to BGP, preventing hijacks and leaks. Learn how ROAs, validators, and routers keep routing secure.
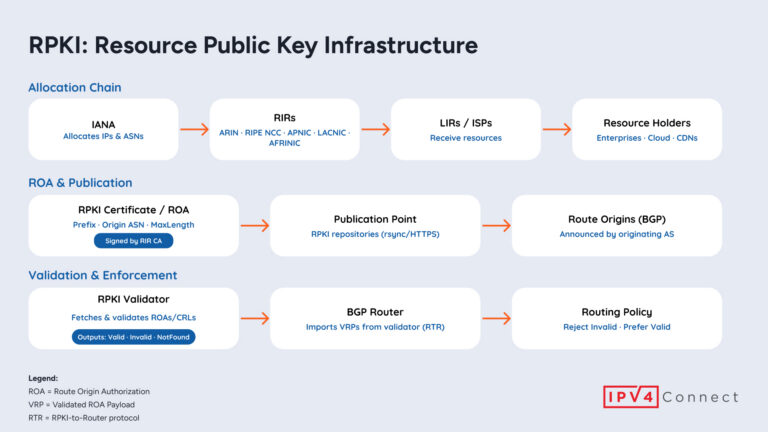
RPKI adds cryptographic trust to BGP, preventing hijacks and leaks. Learn how ROAs, validators, and routers keep routing secure.

Telecom companies face rising cyber threats and espionage, requiring cybersecurity strategies to protect infrastructure, data, and reputation

Transport Layer Security (TLS) is a cryptographic protocol that secures internet communications between servers, browsers, and applications.

IANA, The Internet Assigned Numbers Authority, manages global IP addresses, DNS root zones, and protocols, ensuring internet stability

DDoS attacks overwhelm networks with traffic to cause disruption. This can be mitigated through proactive security measures.
Email me when new IPv4 inventory matches my criteria.
Error: Block data unavailable.
You’ll now receive email alerts when new IPv4 inventory matches your preferences.
Are you absolutely sure you want to delete your account? This action cannot be undone.