What is TLS?
Transport Layer Security (TLS) is a security protocol standard that ensures privacy and data integrity for communications over the Internet. TLS is widely used to secure web applications, encrypting the data exchanged between web browsers and servers. In addition to web traffic, TLS also protects email communications, messaging, and Voice over IP (VoIP) services.
TLS launched in 1999 as an evolution of the older Secure Sockets Layer (SSL) protocol. Since then, it evolved through multiple updates, with the most recent version being TLS 1.3, which was published in 2018. Each new version improves security while enhancing performance, making TLS a fundamental part of modern web security.
The Difference Between TLS, SSL, and HTTPS
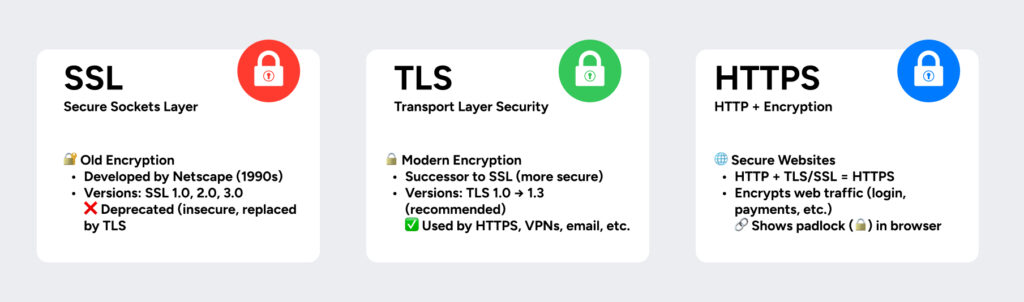
Netscape, an early web browser, originally developed SSL, which later evolved into TLS. Although SSL is now obsolete, many people still refer to TLS as “SSL.” TLS has replaced SSL, offering stronger encryption and improved security mechanisms.
Meanwhile, HTTPS (Hypertext Transfer Protocol Secure) secures HTTP by using TLS encryption. When a website uses HTTPS, browsers display a padlock icon in the address bar to indicate a secure connection between the server and the client.
Why Businesses and Web Applications Need TLS
With the increasing number of cyber threats, implementing TLS is no longer optional for businesses and web applications. Here are some key reasons why TLS is essential:
- Data Protection: TLS encrypts data in transit, preventing unauthorized access and protecting sensitive information.
- Authentication: It ensures that users are communicating with the intended website and not a fraudulent one.
- Data Integrity: TLS verifies that transmitted data remains unchanged during transmission.
- User Trust and Compliance: Browsers now flag non-HTTPS sites as “Not Secure,” which can discourage visitors. Many regulatory standards, such as GDPR and PCI DSS, require TLS encryption for data protection.
How TLS Works
TLS operates through a series of processes to establish a secure connection, mainly involving the TLS handshake, encryption, and authentication.
1. The TLS Handshake
The TLS handshake is an initial process that occurs when a client (such as a browser) connects to a web server. It involves:
- Agreeing on the TLS version to be used (e.g., TLS 1.2 or TLS 1.3).
- Selecting encryption algorithms (cipher suites).
- Authenticating the server using a TLS certificate.
- Generating session keys for encrypting the data.
2. Encryption and Public Key Cryptography
TLS uses asymmetric encryption during the handshake and symmetric encryption for the main communication. Asymmetric encryption involves a public key (shared openly) and a private key (kept secret). Once the handshake is complete, symmetric encryption is used to secure data transmission efficiently.
3. Authentication and Integrity
TLS certificates are issued by trusted certificate authorities (CAs) and are used to verify the authenticity of a website. In addition, TLS uses message authentication codes (MACs) to ensure that data is not altered during transmission.
Performance Impact of TLS
Some people worry that TLS may slow down web applications, but developers have optimized modern implementations for performance. Technologies like TLS False Start and TLS Session Resumption reduce latency. TLS 1.3 further improves speed by using fewer handshake steps than earlier versions.
Implementing TLS on a Website
To use TLS, a website must have a TLS certificate (also called an SSL certificate). These can be purchased from a third party and implemented, and many web hosting providers offer free TLS certificates. OpenSSL is an open-source toolkit for SSL/TLS protocols and cryptographic functions like encryption and certificate management. It’s widely used in web hosting platforms like cPanel to secure data transmission and manage SSL certificates. Those without such services can purchase a certificate from a certificate authority and install it on their web server.